TouchID, Network Mount Blocking, Menu Bar Item, Co-Branding, and More
We’re excited to announce the latest Santa release! This version includes powerful new controls to secure endpoints, including expanded CEL policies that enable requiring TouchID for executions, the ability to block mounting network shares, a menu bar item to help users control common Santa tasks without having to go to the command line, co-branding, and additional usability and performance improvements.
Require TouchID for Binary Execution (Requires Workshop)
One of the most significant additions in this release is the ability to gate execution behind TouchID, ensuring that a user really is at the machine and intended to run the application, adding a critical layer of protection for sensitive applications.
How It Works
When a CEL rule returns REQUIRE_TOUCHID or REQUIRE_TOUCHID_ONLY, Santa will prompt the user for TouchID authentication before allowing the binary to run. This is particularly useful for:
- Privileged administrative tools — Ensure only the person physically present at the machine can run tools like
osascript. - Sensitive applications — Protect access to applications that handle confidential data.
- High-risk binaries/flags — Add friction before executing binaries that could cause significant impact, such as starting
ncwith the listen flag.
Unlike a regular block, when an execution happens that requires authentication it is suspended until authentication is given, so the user does not need to rerun the application.
Configuration Options
Workshop now supports several TouchID-related return values in your CEL rules:
| Function | Description |
|---|---|
REQUIRE_TOUCHID | Require TouchID authentication before execution |
REQUIRE_TOUCHID_ONLY | Require TouchID and skip the normal Santa dialog |
require_touchid_with_cooldown_minutes(N) | Require TouchID with a specified cooldown period, allowing future executions within that period without requiring extra authentication |
require_touchid_only_with_cooldown_minutes(N) | Same as above, skipping the normal Santa dialog |
The cooldown variants are especially useful for applications that users run frequently throughout the day—you get the security benefit of biometric verification without excessive authentication fatigue.
Note: This feature requires Workshop 2026.1 or later.
Network Mount Blocking (Requires Workshop)
This release introduces network mount blocking controls, giving admins the ability to restrict access to mounting network file shares, which can be a vector for data exfiltration or lateral movement. At present this only works with local network mounts, such as NFS and Samba shares. We plan to enhance this in future releases.
Configuration
Network mount blocking is configured in Workshop and configuration can apply as granularly or coarsely as needed, allowing you to apply different policies to different groups of hosts. The configuration options include:
| Option | Description |
|---|---|
| Enable/Disable blocking | Turn network mount blocking on or off for specific tags or globally |
| Host allowlist | Specify trusted network hosts that should always be allowed (e.g., your corporate file servers) |
| Custom block message | Configure the message users see when a mount is blocked |
Use Cases
Network mount blocking is particularly valuable for:
- Preventing unauthorized file sharing — Block access to personal cloud storage services mounted as network drives
- Compliance requirements — Enforce policies that restrict where corporate data can be accessed
- Reducing attack surface — Limit the ability for compromised hosts to mount attacker-controlled shares
Combined with Workshop’s existing USB blocking capabilities (now unified in the UI), you have comprehensive control over removable and network storage across your fleet.
Note: This feature requires Workshop 2026.1 or later.
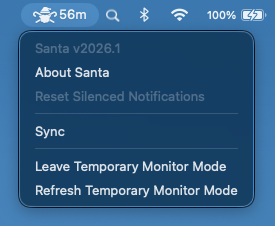
Menu Bar Item
Santa now has a menu bar item that provides users with quick access to common actions. This can be very useful for users who are less familiar with interacting with the terminal, providing the ability to perform syncs or reset notifications that had been silenced.
For Workshop customers who make use of On-Demand Monitor Mode, the menu bar item is a simple way to enter or exit monitor mode and the icon changes to show the amount of time remaining before the machine will revert to Lockdown Mode, providing the opportunity to refresh the requested time before the session expires.
The menu bar item will display by default, but admins can change this default with a new configuration profile setting: EnableMenuItem. Users can control whether to display the menu bar item from a checkbox setting in the “About” dialog.
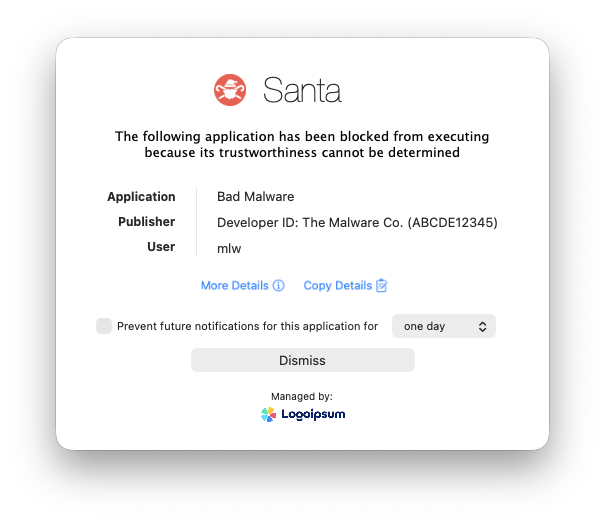
Co-Branding
Admins can now configure their company name or logo to be displayed on Santa UI elements. This can help users with less familiarity with Santa be confident that the software is meant to be on their systems.
Configuration
The following configuration profile keys are supported:
| Option | Description |
|---|---|
| BrandingCompanyName | The name of the company that will appear on Santa UI elements |
| BrandingCompanyLogo | The company logo that will appear on Santa UI elements. If set, this will override BrandingCompanyName. |
| BrandingCompanyLogoDark | The company logo that will appear on Santa UI elements. If set, this will override BrandingCompanyName and BrandingCompanyLogo when UI is displayed in dark mode. |
Additional Improvements
Code Signature Verification
When Santa applies execution rules, it considers various runtime attributes that can affect which rule types are considered. For example, runtime codesigning flags might indicate a binary is not valid, which would prevent rule types such as Team ID or Signing ID from being considered. The new santactl fileinfo --verify flag performs a code signature verification and a Gatekeeper security assessment to help diagnose why Santa might not be applying a rule as expected.
Santa Kill Command (Requires Workshop)
Often you may need to terminate a running process either for compliance reasons or because it’s malicious. Workshop now supports Santa’s Kill Command, allowing administrators to remotely terminate processes on managed hosts. This powerful capability is protected by Workshop’s new Multi-Party Approval (MPA) system—when MPA is enabled, kill commands require approval from multiple administrators before execution, preventing accidental or unauthorized use of this destructive action.
We’re committed to giving you the tools you need to secure your Mac fleet effectively. As always, we welcome your feedback and suggestions for future improvements.